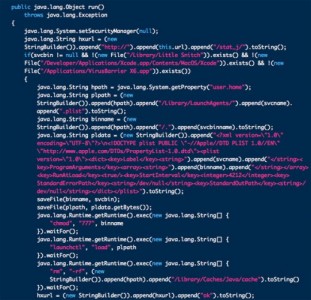
Although many thought that the problems generated by Flashback remained only an ugly memory, here it is Intego discovered a new version of the malware that caused so many problems. The new version is called Flashback.S, it takes advantage of Java vulnerabilities to infect Macs, but is careful not to exploit computers that have VirusBarrier X6, Xcode or Little Snitch applications installed. As soon as the malware infects the Mac, it deletes its files used for infection and gives full access to your Mac.
Intego has discovered a new variant of the Flashback malware, Flashback.S, which continues to use a Java vulnerability that Apple has patched. No password is required for this variant to install, and it places its files in the user's home folder, at the following locations:
- ~/Library/LaunchAgents/com.java.update.plist
- ~/.jupdate
It then deletes all files and folders in ~/Library/Caches/Java/cache in order to delete the applet from the infected Mac, and avoid detection or sample recovery.
Of course, this version of the malware does not need a password to infect your Mac and it uses a vulnerability already blocked by Apple, so theoretically you should be protected if you have made the latest updates for Mac OS X I don't know how many Macs are really infected, but the "telenovela" Flashback seems to be one that is behind not only independent hackers.