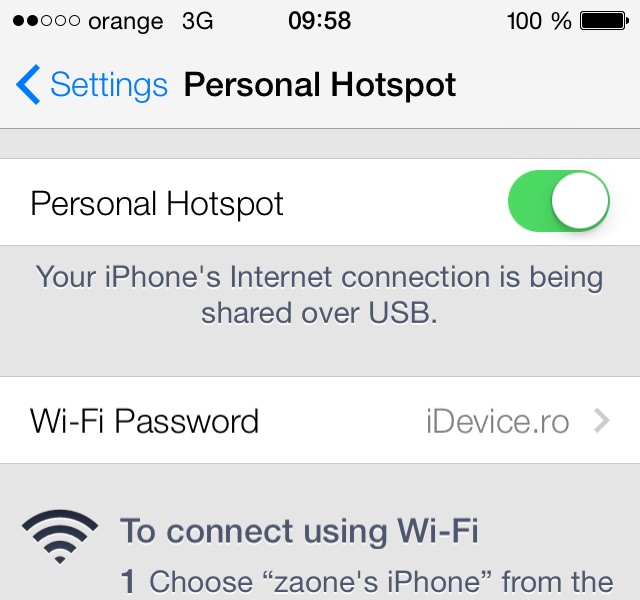
Personal HotSpot is a system implemented by Apple Lossless Audio CODEC (ALAC), about 2 years ago, and it allows us to turn iDevices into real ones Wi-Fi HotSpot-s to share a mobile data internet connection with other devices. Although Apple Lossless Audio CODEC (ALAC), praise the security of its operating system, it seems Personal HotSpot- does not benefit from the same thing, the researchers of the University of Nuremberg discovering that passwords set for this system can be exploited by brute force attacks. More precisely, a script can check millions of passwords for Personal HotSpot before discovering the correct one, the system designed by Apple not having a mechanism to block attempts after entering a few wrong combinations.
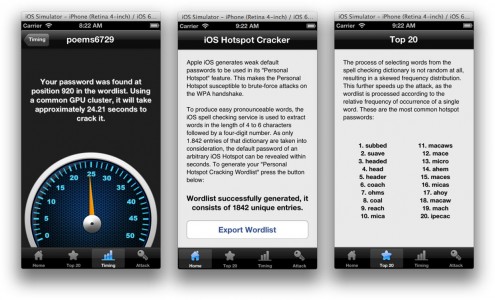
Moreover, the dictionary in iOS contains only 1842 words based on which it chooses passwords, and some of the words included in passwords are chosen much more often than others, 18.5 million possible combinations can be tried by hackers. Based on these vulnerabilities, the researchers claim that a password can be broken in no less than 50 seconds (minimum) with the help of an application designed by them and called iOS HotSpot Cracker, it being available for download following this link. The time period may vary depending on the chosen password and the terminal used for operation.
To automate the process of word list generation, we built the iOS app Hotspot Cracker. This app assists in generating an iOS hotspot cracking word list, which might be used in subsequent attacks on other hotspot users. The app also gives explanations and hints on how to crack a captured WPA2 handshake using well-known password crackers. Future releases might also automate the process of capturing and cracking hotspot passwords. As computing power on smart devices is limited, one solution is to involve online password cracking services like CloudCracker, to crack hotspot passwords on-the-fly.
Theoretically, regardless of the security method used to protect the HotSpot, the application can crack the password only based on recently used word combinations and words available in the iOS dictionary, but the procedure can take between 25 seconds (using 4 graphics cards AMD Radeon HD 7970) and a few days, using only iDevices. No matter how we look at the situation, the Personal HotSpot system is not an extremely important one, but it should still be protected.