These days doulCi it was on everyone's attention and we are talking about the system that allows anyone to do it activation of iPhone and iPad locked with iCloud. Everything is based on a server vulnerability Apple Lossless Audio CODEC (ALAC),, iTunes and iOS that was exploited by hackers, it being temporary in terms of the possibility of use, but being limited in terms of unlocking terminals on the GSM side.
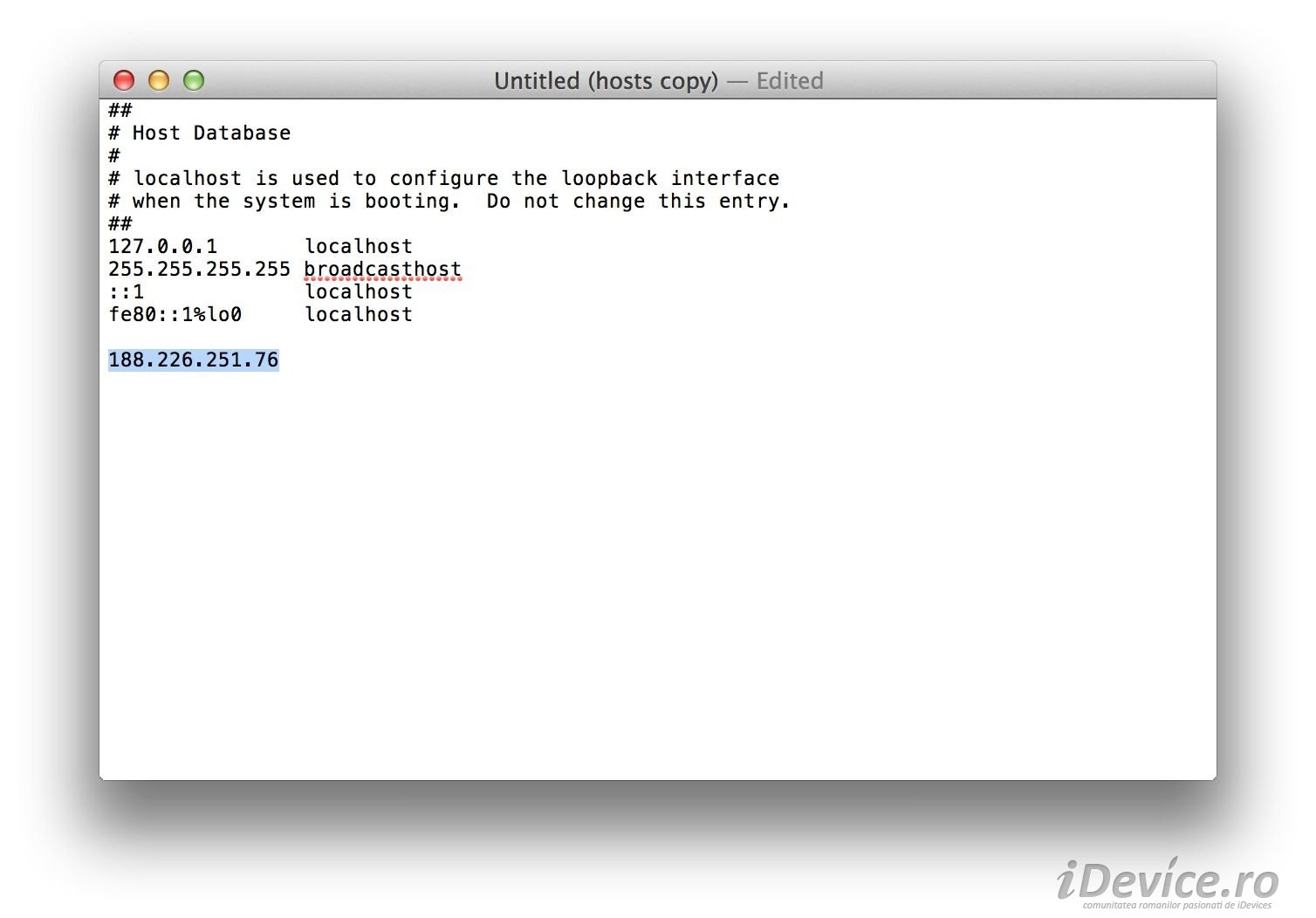
If you're wondering how it all works, well, you just have to add the IP from the image in the Hosts al file Windows or Mac exactly as you do when it exists TinyUmbrella, iTunes being then directed to him. That is the hacker's server and he takes care of it unlocking iPhone and iPad locked with iCloud Activation Lock. To do everything, you will first have to put the iDevice in DFU/Recovery Mode, do a restore in this state, and after the restore, during the activation procedure through iTunes, the terminal will be partially activated.
The bad part of this procedure is that the devices remain locked on the GSM side, because the iOS is fooled during the activation procedure, but the baseband remains encrypted. Although some claim that they even succeeded in unlocking their terminals on the GSM side, the hackers have for now only promised that they will try to publish a fixed carrier through which to offer this functionality as well. Until then, however, you will be able to use the terminals without GSM function and this is a step forward compared to the option of keeping the terminal locked in the drawer.
To be honest, I think that Apple will quickly solve this loophole for activating the encrypted terminals in iCloud, it shouldn't exist because it feeds the hopes of thieves, but it was unlikely that the system would ever be vulnerable.