Compania Apple a fost in repetate randuri prezenta la conferintele Black Hat din Las Vegas, oamenii sai find mai mereu in audienta pentru a participa la prezentarile care au loc acolo, insa pana anul acesta cei din Cupertino nu au tinut o conferinta proprie pentru a discuta despre securitatea sistemului de operare iOS.
In cursul noptii trecute Ivan Krstic, seful diviziei de securitate din cadrul Apple, a discutat despre munca depusa de catre inginerii celor din Cupertino pentru a securiza iDevice-urile vandute de catre compania Apple, la finalul conferintei el anuntand si un program prin care Apple va plati bani pentru bugurile descoperite in iOS.
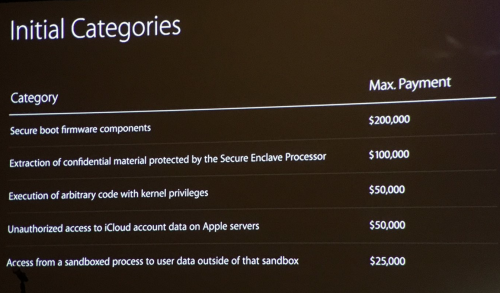
Mai exact, Apple va plati urmatoarele sume de bani pentru bugurile descoperite in :
- Secure boot firmware: $200,000
- Extraction of confidential material protected by the Secure Enclave Processor: $100,000
- Execution of arbitrary code w/kernel privs: $50,000
- Unauthorized access to iCloud account data on Apple Servers: $50,000
- Access from a sandboxed process to user data outside of that sandbox: $25,000
Cea mai mare suma oferita de catre compania Apple pentru vulnerabilitati descoperite in iOS este de 200.000 de dolari pentru un bug care sa permita pornirea nesecurizata a sistemului de operare, iar doar 100.000 de dolari sunt oferiti pentru extragerea de date din enclava securizata in care sunt stocate amprentele utilizatorilor.
Desi cei de la Apple au facut un pas in directia potrivita si ofera bani pentru vulnerabilitati, sumele oferite de catre ei sunt cu mult mai mici fata de cele pe care le platesc agentii guvernamentale din diverse tari, hackerii obtinand chiar si peste 1 milion de dolari pentru exploit-uri suficient de bune pentru iOS.
Lasand astea la o parte, conferinta companiei Apple in cadrul Black Hat s-a numit BEHIND THE SCENES OF IOS SECURITY, iar mai jos aveti prezentate cateva puncte importante din cadrul sau :
With over a billion active devices and in-depth security protections spanning every layer from silicon to software, Apple works to advance the state of the art in mobile security with every release of iOS. We will discuss three iOS security mechanisms in unprecedented technical detail, offering the first public discussion of one of them new to iOS 10.
HomeKit, Auto Unlock and iCloud Keychain are three Apple technologies that handle exceptionally sensitive user data – controlling devices (including locks) in the user’s home, the ability to unlock a user’s Mac from an Apple Watch, and the user’s passwords and credit card information, respectively. We will discuss the cryptographic design and implementation of our novel secure synchronization fabric which moves confidential data between devices without exposing it to Apple, while affording the user the ability to recover data in case of device loss.
Data Protection is the cryptographic system protecting user data on all iOS devices. We will discuss the Secure Enclave Processor present in iPhone 5S and later devices and explain how it enabled a new approach to Data Protection key derivation and brute force rate limiting within a small TCB, making no intermediate or derived keys available to the normal Application Processor.
Traditional browser-based vulnerabilities are becoming harder to exploit due to increasingly sophisticated mitigation techniques. We will discuss a unique JIT hardening mechanism in iOS 10 that makes the iOS Safari JIT a more difficult target.